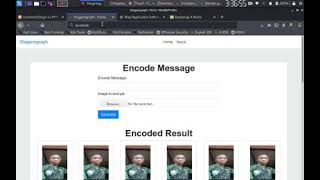
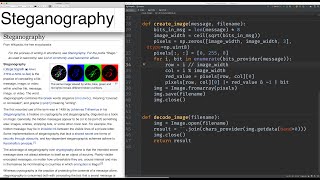
Steganography Tutorials | How To Hide Text Inside Image | Cybersecurity Training | Lecture 46 |

|
|
Secrets of data haiding | Man in the browser attacks | Ethical Hacking with 100% Lab:
Secrets of Data Hiding: Data hiding refers to the practice of concealing data within other types of data in order to protect it from unauthorized access or detection. This can involve techniques such as steganography, which involves hiding data within other types of files, or encryption, which involves using a mathematical algorithm to scramble the data so that it can only be read by someone with the correct decryption key. Man in the Browser Attacks: A Man-in-the-Browser (MitB) attack is a type of malware that infects a web browser and intercepts communication between the user and the website. The attacker can then modify the communication, redirect the user to a fake website, or steal sensitive information such as login credentials, credit card numbers, or personal data. Ethical Hacking with 100% Lab: Ethical hacking is the practice of using hacking techniques to identify vulnerabilities and weaknesses in computer systems in order to improve their security. The 100% lab component refers to the use of practical exercises and simulations to give students hands-on experience with hacking techniques and tools in a safe and controlled environment. This approach allows students to develop their skills and knowledge in a realistic setting while minimizing the risk of causing harm or damage to real-world systems. Keywords: hacking hacking tutorial dark web ethical hacking full course work from home cyber security course ethical hacking phishing tutorial for beginners sms spoofing social engineering hacking sql injection tor browser how to use be site cause moral cybersecurity tutorial ethical hacking course hacking course how to become a hacker how to get a vpn on a school chromebook http proxy information security keylogger android malware analysis onion website phishing attack website link phishing page port targeted individual web scraping what is ip address Data hiding Steganography Encryption Cybersecurity Malware Man-in-the-Browser attacks Web browsers Communication interception Website security Login credentials Password cracking Wireless network security DNS security Firewall Cybercrime Cyber laws Cyber ethics Risk management Information security management Disaster recovery planning Business contin ethical hacking, hacking, ceh, ethical hacking tutorial, browser hacking, ethical hacking course, ethical hacker, simplilearn ethical hacking, 10 hours training of ethical hacking, ethical hacking full course in one video, hacking web browser, ethical hacking career path, cracking, ethical hacking webinar, learn ethical hacking and cybersecurity, ethical hacking free course, ethical hacking career, hacking with a link, ethical hacking workshop, ethical hacking classes, cnet, technology, tech, hackers, atm, financial hack, financial hacker, bank hack, bank hackers, crime, heist, robbery, money hack, atm hackers, atm hack 2019, hack pro, money, money heist, black hat 2019, black hat hacker, black hat hacking, black hat, professional hacker, jackpot, atm hacking, atm jackpotting, atm jackpotting video, black hat atm jackpotting, certified ethical hacker, data security, certprime, cyber security Hasntags: #datahiding #steganography #encryption #cybersecurity #malware #ManInTheBrowser #webbrowsers #communicationinterception #websitesecurity #logincredentials #creditcardnumbers #personaldata #ethicalhacking #computersystems #vulnerabilities #securitytesting #pentesting #networksecurity #webapplicationsecurity #operatingsystemsecurity #vulnerabilityassessment #exploitation #socialengineering #passwordcracking #wirelessnetworksecurity #DNSsecurity #firewall #intrusiondetection #webserversecurity #VPN #regulatoryrequirements #physicalsecurity #accesscontrols #authentication #authorization #cryptography #publickeyinfrastructure #digitalcertificates #securitypolicies #securitystandards #securityframeworks #securitycontrols #securityassessments #securityawareness #securityeducation #securitygovernance #threatmodeling For more details, Our facebook page: https://facebook.com/hacorial Our youtube channel : https://youtube.com/@hacorial -------------------------- Copyright Related Issue Please Contact mdh741@gmail.com -------------------------- If You Like the vedio then, Don't Forget ??Like ?? ??Comment & ??Please Subscribe our channel --------------------------- Background Voice - ****AI VOICE**** ------------------------ Video credit : Pexels https://www.pexels.com Pixabay https://pixabay.com https://chat.openai.com ------------------------ "Thanks For Watching" -~-~~-~~~-~~-~- Please watch: "Ethical Hacking Trainning || CEH || INTRODUCTION TO ETHICAL HACKING || Lecture 02" https://www.youtube.com/watch?v=44vB6EVrLB0 -~-~~-~~~-~~-~- |