Diffie Hellman | NodeJS | End-to-end Encryption |

|
|
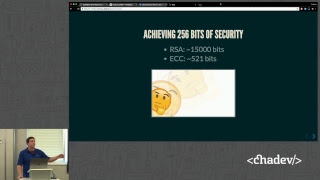
In this video you will learn the how to implement #Diffie-Hellman key exchange, to generate a shared secret between two clients, which then can be used to exchange #end-to-end encrypted messages. The implementation is inside a nodejs application, we will be using the #crypto module which is built inside #nodejs.
⭐ Kite is a free AI-powered coding assistant that will help you code faster and smarter. The Kite plugin integrates with all the top editors and IDEs to give you smart completions and documentation while you’re typing. I've been using Kite for 6 months and I love it! https://www.kite.com/get-kite/?utm_medium=referral&utm_source=youtube&utm_campaign=yourstruly&utm_content=description-only Github(Diffie-Hellman tutorial): https://github.com/trulymittal/diffie-hellman-shared-secret Diffie–Hellman key exchange(Wiki): https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange MODP DH Groups: https://www.ietf.org/rfc/rfc3526.txt Wikipedia (primitive root modulo): https://en.wikipedia.org/wiki/Primitive_root_modulo_n ——————————————— Other useful Videos ——————————————— Diffie Hellman analogy: https://youtu.be/JnZQMUL8GcQ Diffie Hellman Mathematics: https://youtu.be/8Pk8pdHfEy4 Diffie Hellman Nodejs: https://youtu.be/TzOFFV1beTw Elliptic-Curve Diffie-Hellman (ECDH): https://youtu.be/VV7x4tMxeoI AES (Advanced Encryption Standard): https://youtu.be/79kuLT5HWs0 ECDH + AES 256 (CBC): https://youtu.be/l5eLUzYzpd8 ECDH + AES 256 GCM (Authenticated Encryption): https://youtu.be/M7M3qeQxTq4 ——————————————— Other useful Playlists ——————————————— Docker: https://www.youtube.com/playlist?list=PLdHg5T0SNpN0gFlL8AXvZdAHsvpkuW0Ba MongoDB: https://www.youtube.com/watch?v=liocKBCVJyw&t=7s Html/Css/Js: https://www.youtube.com/playlist?list=PLdHg5T0SNpN0saXVT9gfb2MESkiHG8YbP Android: https://www.youtube.com/playlist?list=PLdHg5T0SNpN2cv8zhK-zQx2qXfJKap9kU Firebase: https://www.youtube.com/playlist?list=PLdHg5T0SNpN2NimxW3piNqEVBWtXcraz- Challenges: https://www.youtube.com/playlist?list=PLdHg5T0SNpN20F2v0xYWeLRZtdehexzDi ——————————————— What I use ——————————————— Mouse: https://amzn.to/2O9RJtu Keyboard: https://amzn.to/2qxajCU Keyboard 2: https://amzn.to/2XDWH4X Monitor: https://amzn.to/2pDg7dH Processor: https://amzn.to/347WWIb RAM: https://amzn.to/2QEkUqw Graphics: https://amzn.to/33aBrF4 Microphone: https://amzn.to/2DabdI9 |