Lifting The Veil Of The Dark Web |

|
|
See How Companies Arm Themselves With The Right Tools To Protect Against Threats From The Dark Web.
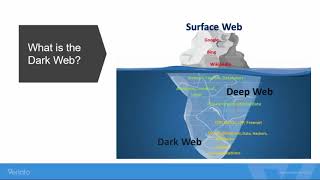
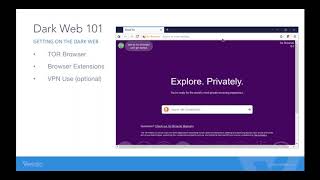
We've all seen what's possible with the Dark Web thanks to Silk Road. If you're interested in buying or selling someone's personal data, such as credit card or social security information, it’s disturbingly easy to do. All you need is a computer and the Tor Browser, and it's all completely anonymous. So how do companies arm themselves with the right tools to protect themselves against rogue access to the Dark Web? Join Alex Courson from Veriato and Natasha Boyko from ID Agent as they discuss topics such as: Dark Web 101: Understand the basics How do leading organizations leverage technology to combat cybercrime and fraud enabled by the Dark Web? Are your employees being recruited by crime syndicates on the Dark Web? What can companies do to eliminate these threats? |