BSides Lisbon 2016 - Introducing Man In The Contacts attack to trick encrypted messaging apps |

|
|
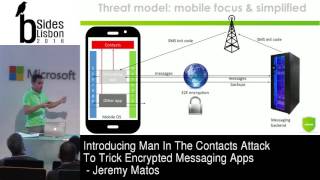
Mobile messaging applications have recently switched to end-to-end encryption. With debates at the government level to ask for backdoors, those tools are perceived as unbreakable. Yet, most of the implementations trust the contact information stored in the smartphone. Given that end-users hardly know a few phone numbers and that modifying contacts is easy, we will introduce a new type of attack: Man In The Contacts (MITC).
Without studying any cryptography, we will examine how WhatsApp, Telegram and Signal behave when an Android application is tampering with the contacts in background. For some scenarios, the end-user can be fooled in talking to the wrong person and a MITM proxy can be implemented. Finally, we will discuss about countermeasures both at the technical and usability levels. About the Speaker: Jérémy Matos has been working in building secure software over the last 10 years. With an initial academic background as a developer, he was involved in designing and implementing a two-factor authentication product with challenging threat models, particularly when delivering a public mobile application. As a consultant he helped in the security requirements definition and implementation, including cryptographic protocols, for applications where the insider is the enemy. He also led code reviews and security validation activities for companies exposed to reputation damage. In addition, he participated in research projects to mitigate Man-In-The-Browser and Man-In-The-Mobile attacks. |






![[BSL2022 Keynote] A brief history of IOT security - Elisa Costante](https://ytimg.googleusercontent.com/vi/HhTkV0qcpu8/mqdefault.jpg)









![[BSL2019] A Special Class Of Stream Cipher Backdooring Techniques - Eric Filiol](https://ytimg.googleusercontent.com/vi/GrjxfbR--CU/mqdefault.jpg)